Post operations
View post schedules
- Permission
- View post
- Min. clearance
- None
- Has permission?
- No
- Meets clearance?
- Yes
Stay audit-ready with automated task tracking, robust access control, and audit trails.
Schild enforces dual-layer security: users must have both the required role-based permission and meet the minimum sensitivity clearance. Access is denied if either requirement fails.
User has required permission and meets clearance level
User lacks the required permission
User's clearance is below the minimum required
Below are access evaluations for various data types using this user context.
View post schedules
Sensitive report content
Organization policies
Clearance hierarchy: None → Controlled, unclassified → Confidential → Secret → Top secret
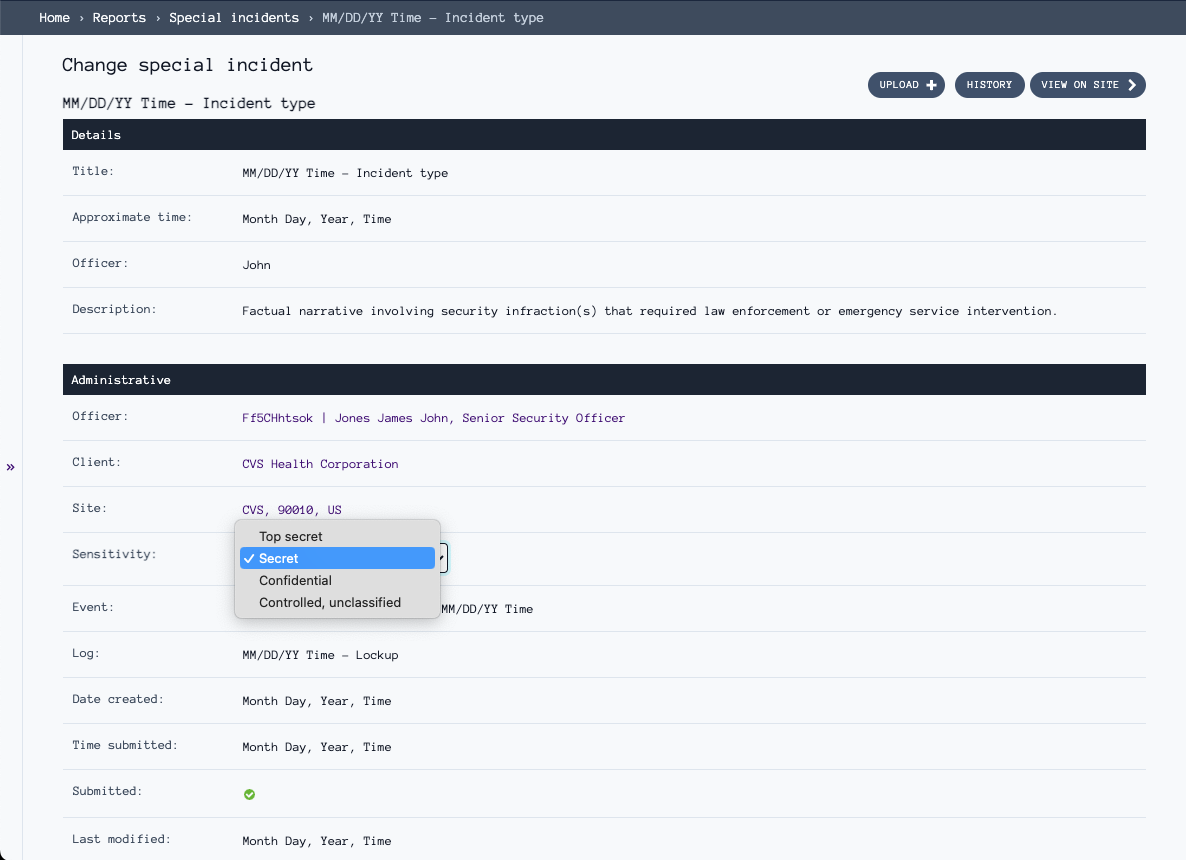
Document special incidents that require law enforcement or emergency service contact with sensitivity controls. Set clearance levels from "Controlled, unclassified" to "Top secret" to ensure only authorized personnel can view sensitive incident details and officer narratives.
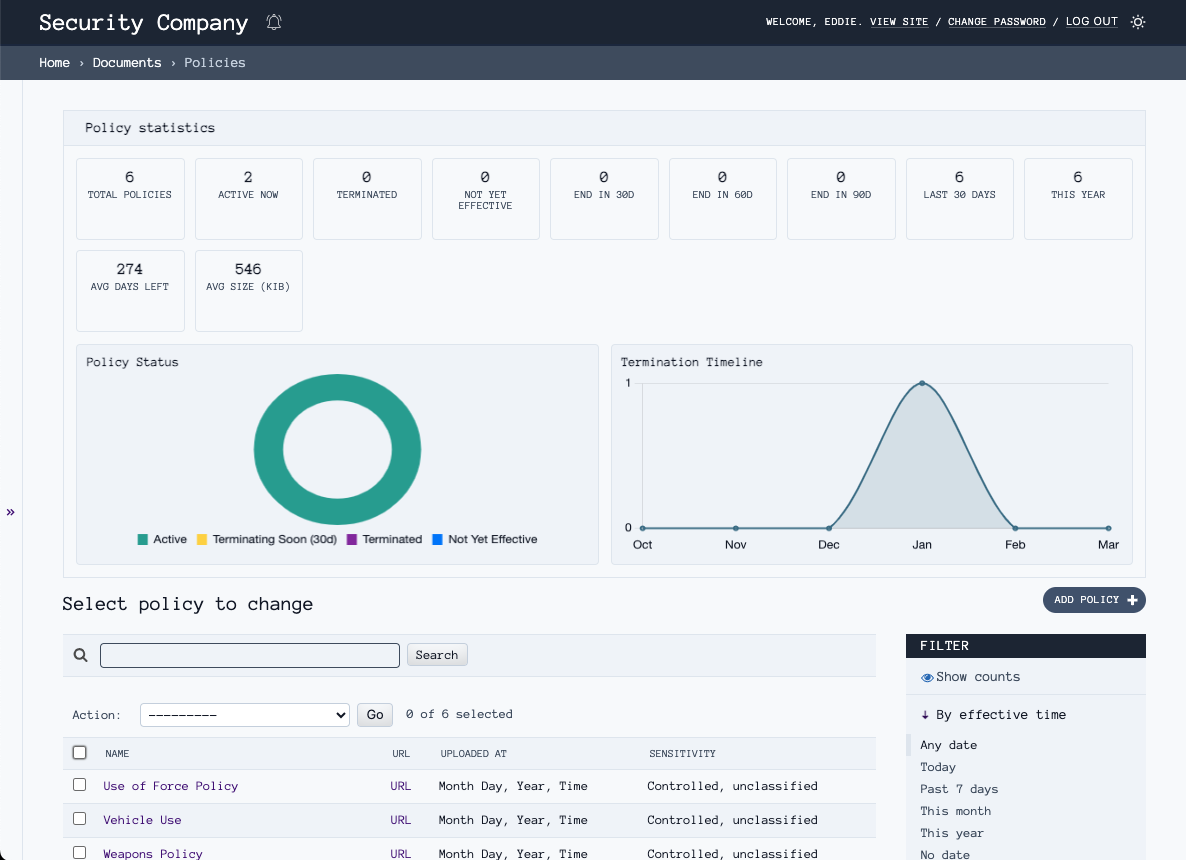
Stop hunting through emails for policy documents. Centralize all organizational policies in one system with role-based access controls and automated distribution. Know at a glance which policies are active, expiring, or outdated. When audits or incidents require proof of policy distribution, pull records instantly instead of digging through inboxes.
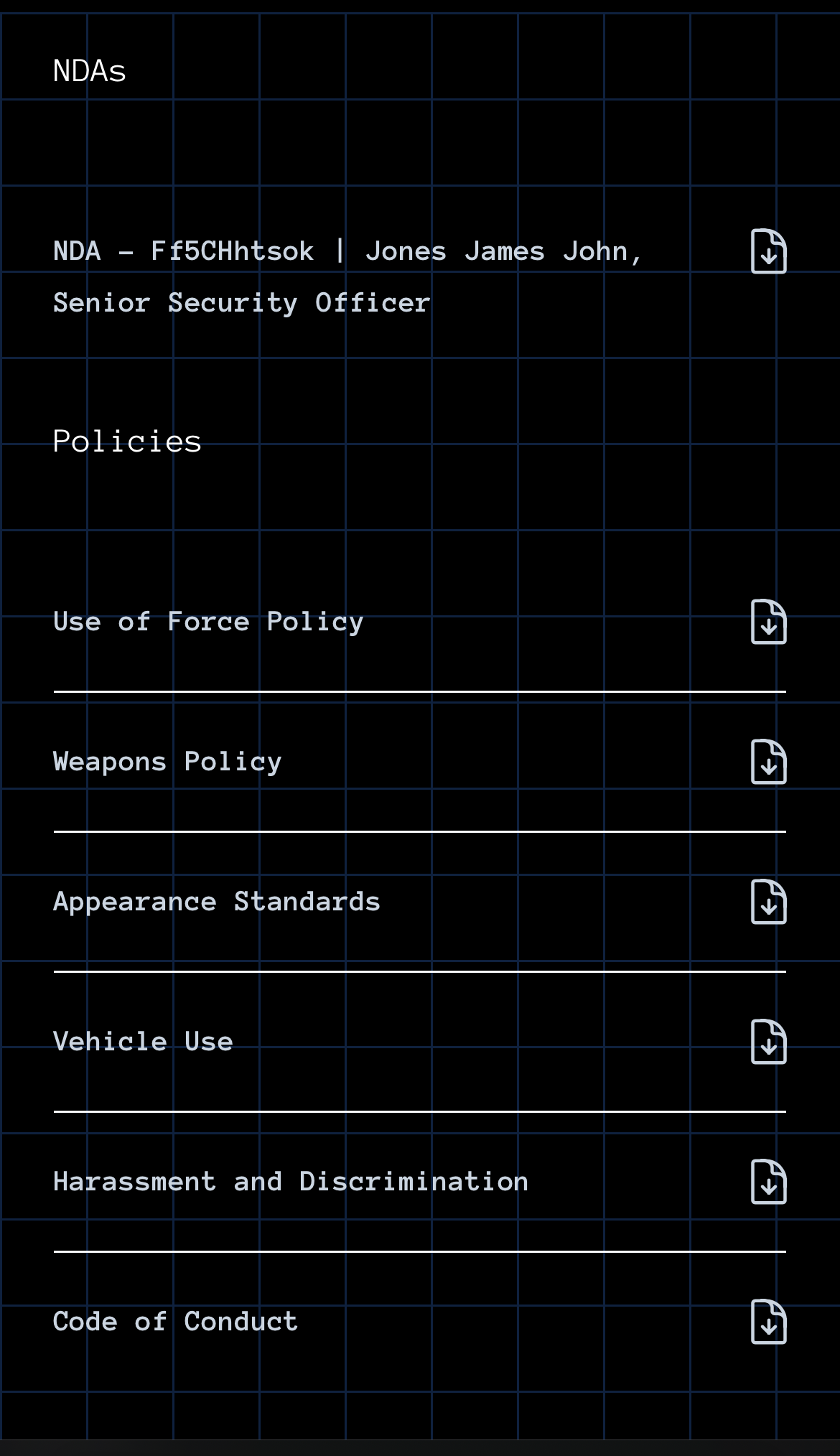
Personnel can access distributed documents quickly from any device. Download and view policies like Use of Force, Weapons, Appearance Standards, and Vehicle Use—with one-tap and click. Whether in the field, at home, or in an office, personnel have what they need, when they need it.
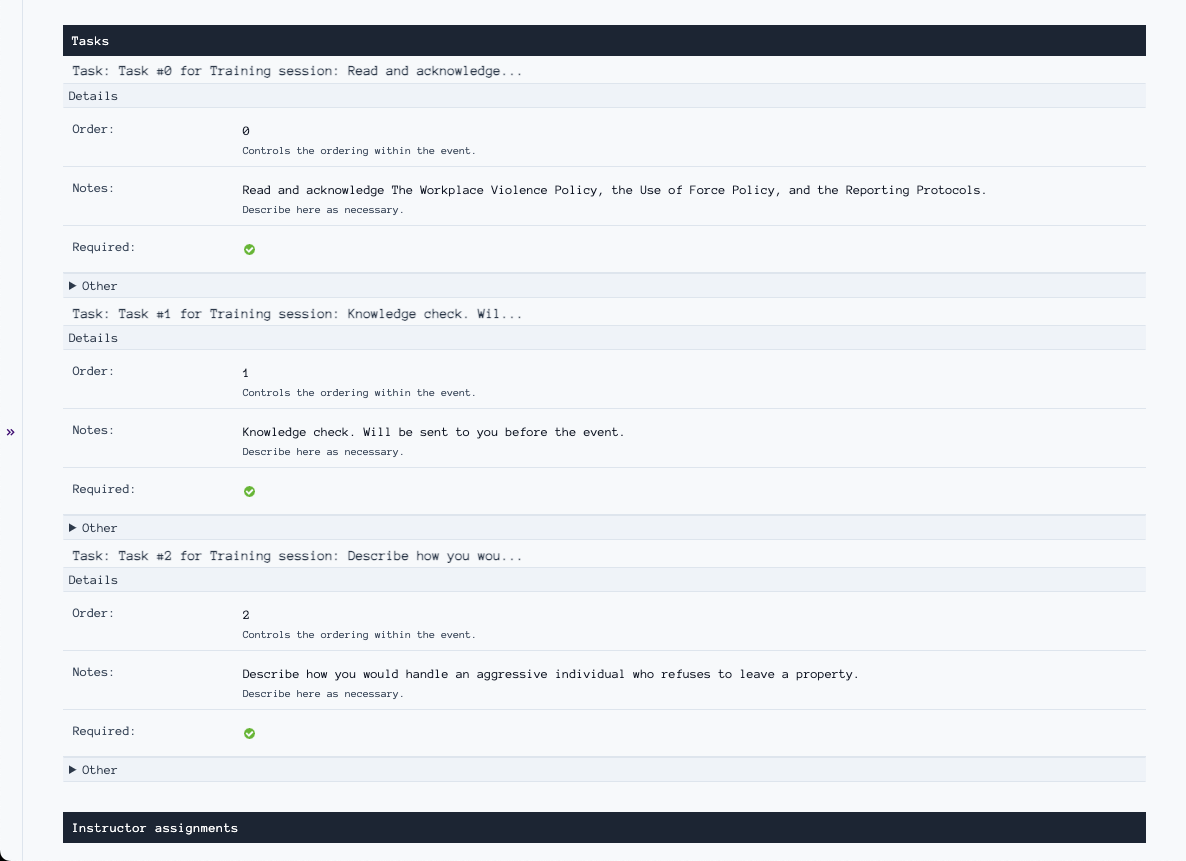
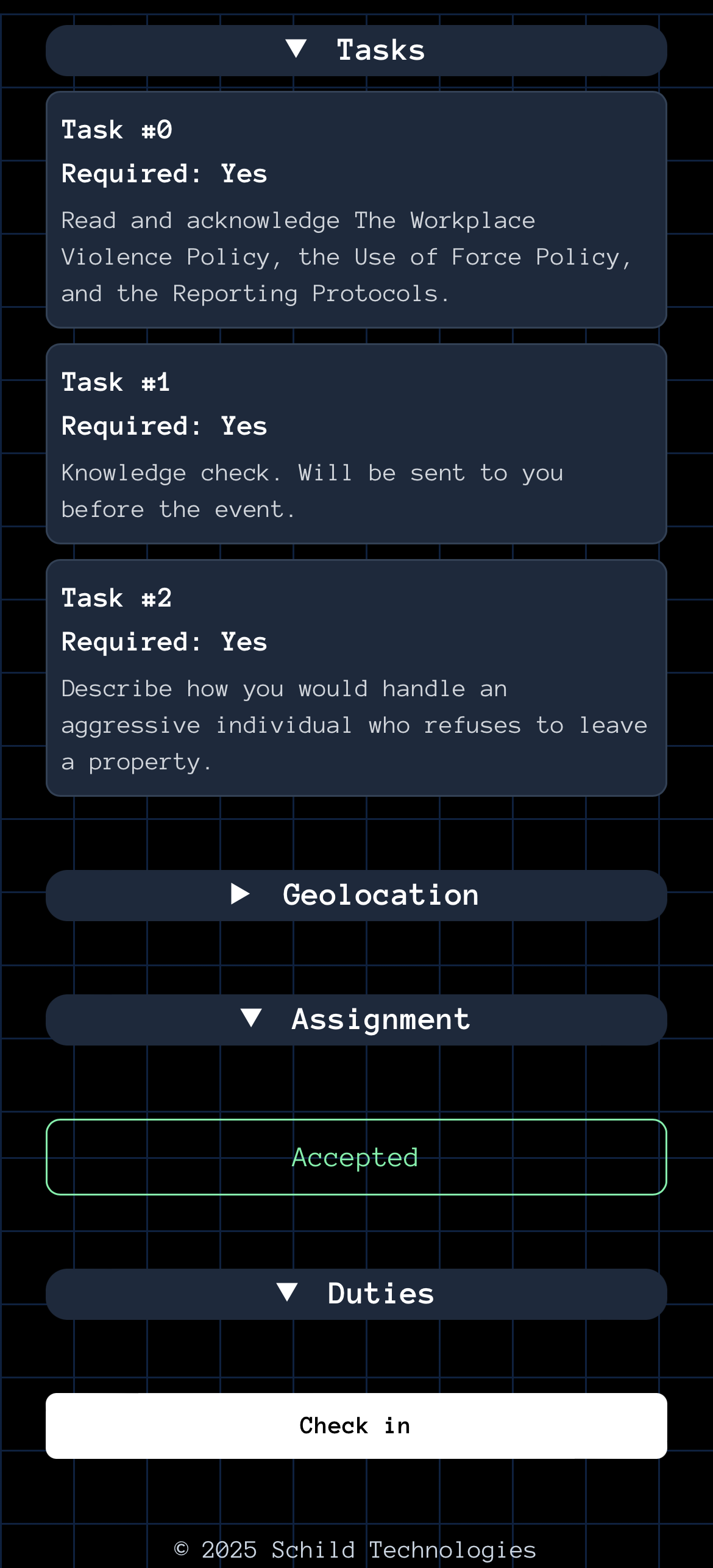
Create ops with required tasks that enforce compliance with internal policies. Set task order, require completion, and track acknowledgments—ensuring personnel read policies, complete knowledge checks, and demonstrate understanding before and during assignments. Be confident your security operations are preventing incidents, not creating them.
Personnel complete training sessions and other ops with ordered tasks including policy acknowledgments, knowledge checks, and scenario responses. Tasks are presented in sequence with clear requirements, file uploading, and timestamps—providing documented evidence of internal compliance.